Search for "374" returned 1967 results

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

30 min
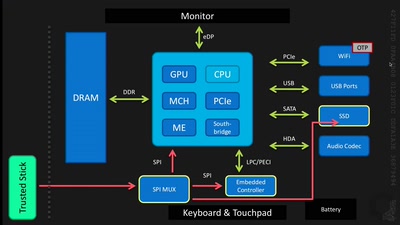
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
apertus° AXIOM
The first Open Source Cinema Camera

54 min
Do You Think That's Funny?
Art Practice under the Regime of Anti-Terror Legislation

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…
59 min
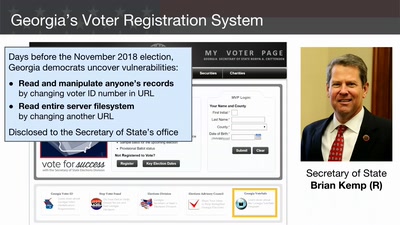
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology
53 min
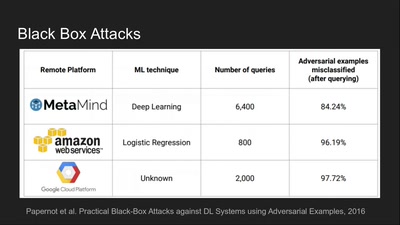
Deep Learning Blindspots
Tools for Fooling the "Black Box"

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

62 min
Netzpolitik in der Schweiz 2016
Grundrechte per Volksentscheid versenken

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy
36 min
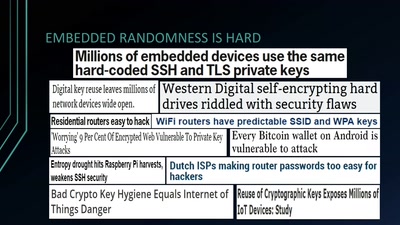
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

34 min
Snowden Effect vs. Privacy Paradox
Einstellungen und Internetnutzungsverhalten im Kontext des…
31 min