Search for "426" returned 2015 results

62 min
Kyber and Post-Quantum Crypto
How does it work?

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
56 min
Making Technology Inclusive Through Papercraft and Sound
Introducing the Love to Code Platform

60 min
Quantum Cryptography
from key distribution to position-based cryptography
61 min
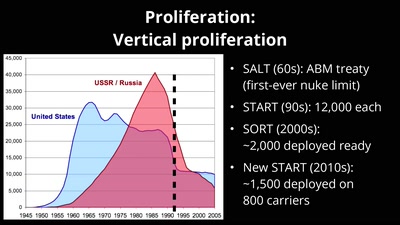
What Ever Happened to Nuclear Weapons?
Politics and Physics of a Problem That's Not Going Away

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

59 min
Security of the IC Backside
The future of IC analysis

46 min