Search for "【"W" returned 10205 results

69 min
Mobile phone call encryption
Encrypting (GSM) mobile phone calls over VPN with an…

95 min
Analysis of a strong Random Number Generator
by anatomizing Linux' CPRNG

49 min
Ethernet mit Mikrocontrollern
Wie funktioniert TCP mit 2kb RAM?

45 min
Secure Network Server Programming on Unix
Techniques and best practices to securely code your network…

87 min
Tor and China
Design of a blocking-resistant anonymity system

47 min
How to implement bignum arithmetic
A short look at my pet project implementation

78 min
Stealth malware - can good guys win?
Challenges in detecting system compromises and why we’re so…

65 min
Body hacking
Functional body modification

54 min
To live outside the law you gotta be honest
Ist nicht jedes Passwort eine Manifestation des Mißtrauens?
57 min
Know Your Citizens
State Authorities' Access to Sensitive Information

76 min
Information Operations
Sector-Oriented Analysis of the Potential Impact and…

46 min
The Rise and Fall of Open Source
The Million Eyeball Principle and forkbombs

44 min
Open Source Machine Translation
From tools, to tricks, to projects: build a translation…
47 min
A not so smart card
How bad security decisions can ruin a debit card design

64 min
Who can you trust?
Opening Ceremony and Keynote

68 min
Data Retention Update
News and Perspectives on Implementation and Opposition

63 min
Transparency and Privacy
The 7 Laws of Identity and the Identity Metasystem

45 min
Introduction to matrix programming: trance codes
How to recognize trance coded communication patterns

52 min
4+2+1 Jahre BigBrotherAwards Deutschland
Eine Lesung aus dem Buch "Schwarzbuch Datenschutz"

98 min
The Grim Meathook Future
How The Tech Culture Can Maintain Relevance In The 21st…
55 min
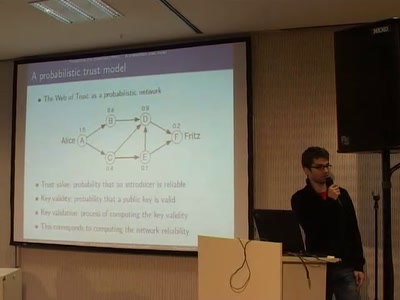
A Probabilistic Trust Model for GnuPG
A new way of evaluating a PGP web of trust by using a…

138 min


