Search for "【"W" returned 10204 results

25 min
Security Log Visualization with a Correlation Engine
What's inside your network?

55 min
Introducing Osmo-GMR
Building a sniffer for the GMR satphones
64 min
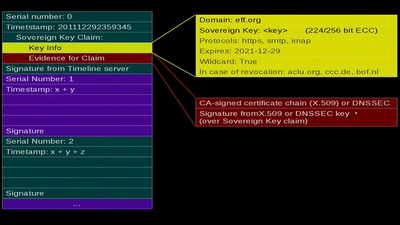
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC
56 min
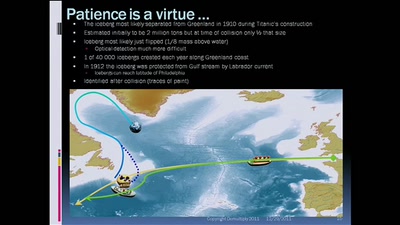
The future of cryptology: which 3 letters algorithm(s) could be our Titanic?
RMS Olympic, RMS Titanic, HMHS Britannic vs Discrete…

59 min
Deceiving Authorship Detection
Tools to Maintain Anonymity Through Writing Style & Current…

59 min
Not your Grandfathers moon landing
Hell yeah, it's Rocket Science 3.1415926535897932384626!

61 min
Electronic money: The road to Bitcoin and a glimpse forward
How the e-money systems can be made better

128 min
Lightning Talks Day 3
Pecha Kucha Round!

63 min
Print Me If You Dare
Firmware Modification Attacks and the Rise of Printer…

43 min
CCC Camp 2011 Video Impressions
Reviving a nice summer dream
53 min
The best of The oXcars
the greatest free/Libre culture show of all times

28 min
Frag den Staat
Praktische Informationsfreiheit
28 min
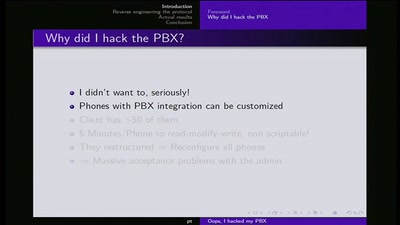
Ooops I hacked my PBX
Why auditing proprietary protocols matters
45 min
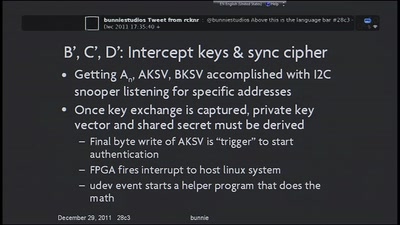
Implementation of MITM Attack on HDCP-Secured Links
A non-copyright circumventing application of the HDCP…

51 min
Apple vs. Google Client Platforms
How you end up being the Victim.

65 min
Quantified-Self and OpenBCI Neurofeedback Mind-Hacking
Transhumanism, Self-Optimization and Neurofeedback for…

63 min
Power gadgets with your own electricity
escape the basement and make the sun work for you
57 min