Search for ".pik" returned 1017 results

58 min
Virtual Machine Introspection
From the Outside Looking In

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols
40 min
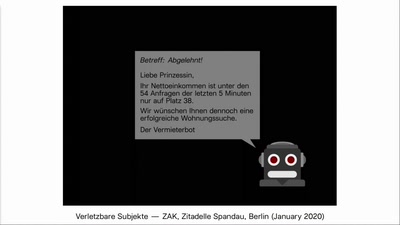
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks
61 min
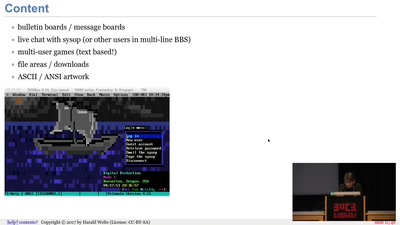
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

29 min
Building and Breaking Wireless Security
Wireless Physical Layer Security & More...
41 min
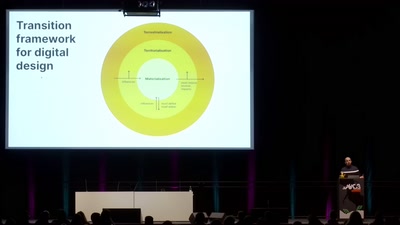
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

58 min
Switches Get Stitches
Industrial System Ownership

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data
57 min
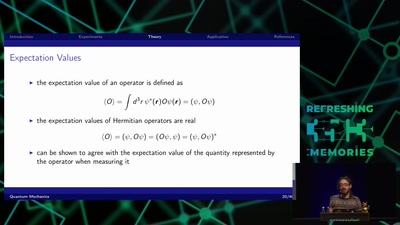
Quantum Mechanics
A Gentle Introduction
41 min
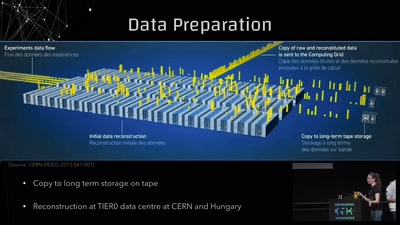
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

61 min
Warum die Digitale Revolution des Lernens gescheitert ist.
Fünf Desillusionen

54 min