Search for "m-1-k-3" returned 9403 results
48 min
GPS-Trackers
How they track you when your mobile is switched off
security in 2006: having phun with it.jpg)
111 min
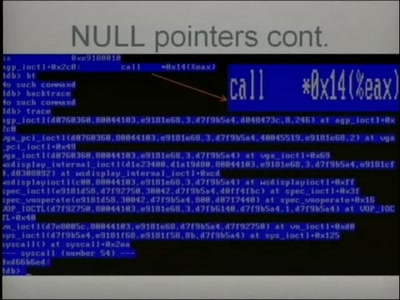
X.25 (in)security in 2006: having phun with it
Actual present, next future & field experiences analysis of…

103 min
Comparison of WAN IGP protocols
RSTP+flooding/learning for Ethernet, OSPFv2 for IPv4, and…

66 min
Podjournalism
The Role of Podcasting in Critical and Investigative…

61 min
CSRF, the Intranet and You
Causes, Attacks and Countermeasures

51 min
Culture Jamming & Discordianism
Illegal Art & Religious Bricolage

68 min
Inside VMware
How VMware, VirtualPC and Parallels actually work

49 min
Mining Search Queries
How to discover additional knowledge in the AOL query logs

58 min
How to squeeze more performance out of your wifi
Cross-layer optimization strategies for long-range IEEE…

40 min
Pornography and Technology
a love affair

52 min
Funkerspuk
radio politics in the USA and Germany in the first half of…

63 min
Counter-Development
The Accessibility of Technology as an Addendum to…

53 min
Fuzzing in the corporate world
The use of fuzzing in the corporate world over the years…
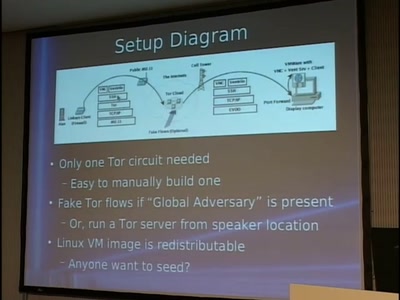
63 min
Rootkits as Reversing Tools
An Anonymous Talk
58 min