Search for "m-1-k-3" returned 9403 results
121 min
Lightning Talks - Day 4
where is my community?
58 min
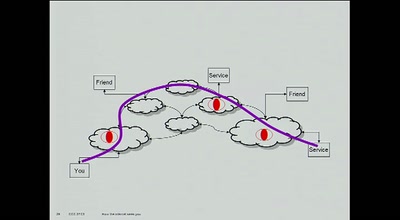
How the Internet sees you
demonstrating what activities most ISPs see you doing on…
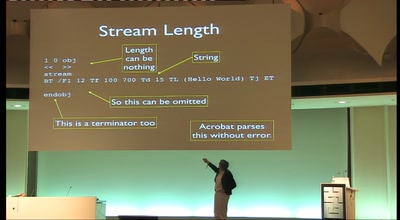
57 min
OMG WTF PDF
What you didn't know about Acrobat
59 min
International Cyber Jurisdiction
Kill Switching” Cyberspace, Cyber Criminal Prosecution &…
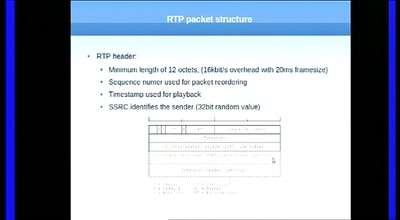
36 min
Having fun with RTP
„Who is speaking???“

64 min
Tor is Peace, Software Freedom is Slavery, Wikipedia is Truth
The political philosophy of the Internet

50 min
Data Analysis in Terabit Ethernet Traffic
Solutions for monitoring and lawful interception within a…
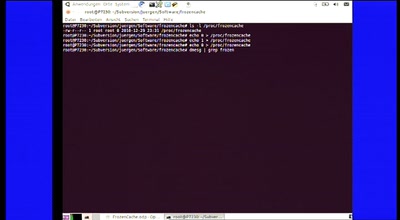
55 min
FrozenCache
Mitigating cold-boot attacks for Full-Disk-Encryption…

58 min
Analyzing a modern cryptographic RFID system
HID iClass demystified

134 min
Hacker Jeopardy
Number guessing for geeks

59 min
Safety on the Open Sea
Safe navigation with the aid of an open sea chart.

61 min
Running your own GSM stack on a phone
Introducing Project OsmocomBB
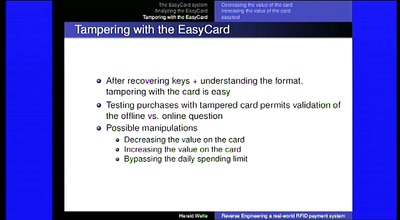
58 min
Reverse Engineering a real-world RFID payment system
Corporations enabling citizens to print digital money
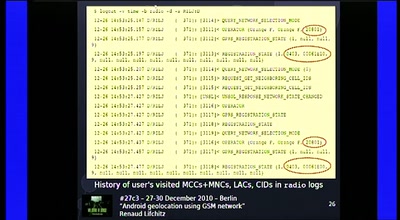
63 min
Android geolocation using GSM network
"Where was Waldroid?"
134 min
Hacker Jeopardy (english translation)
Number guessing for geeks

65 min
Zero-sized heap allocations vulnerability analysis
Applications of theorem proving for securing the windows…

56 min
IMMI, from concept to reality
The Icelandic Modern Media Initiative and our need for a…

25 min