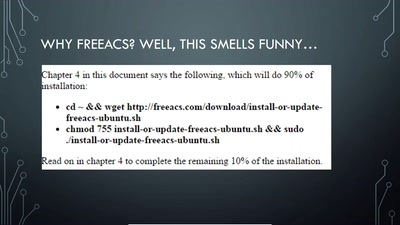
Search for "m-1-k-3" returned 9403 results

38 min
Hardware games
How to build alternative controllers

28 min
Exploiting The North American Railways
Modern Day American Hobo-ism
32 min
Cryptokids
empower kids and provide tools for them to be more secure…

64 min
Fermentation Mobile
experimental, educational and commercial fermentation…

51 min
Anonymous, secure and easy. You can have them all.
An authentication protocol that offers security, privacy…
18 min
Malware: From your text editor, to the United States Government's Lab
How Universities in the US collaborate with the United…

46 min
SHOULD I STAY OR SHOULD I GO?
THE ALGORITHMIC PUBLIC SPHERE AND YOU

47 min
Olmogo - because it's your data!
A cryptographically secure social network platform

40 min
The World in 24 Hours Revisited
How to re-enact a 1982 network art performance
29 min
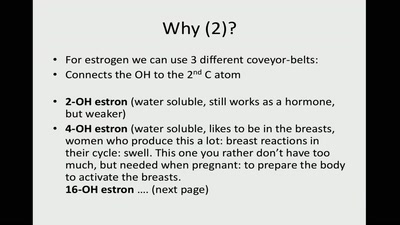
Hormones and Hysteria - what every person should know
are you not curious now? ;)

59 min
Developments in Coordinated Vulnerability Disclosure
The government is here to help

63 min
Data Exploitation
how your digital doppelganger has been exploiting you all…

60 min
Flip Feng Shui
Advanced Rowhammer exploitation on cloud, desktop, and…

61 min
The state of the pretty Easy privacy (p≡p) project and what to expect next
Easy to use automatic encryption for the masses

25 min
Network Traffic Analysis using Deep Packet Inspection and Data Visualization
Eventpad: the Sublime editor for network traffic
59 min
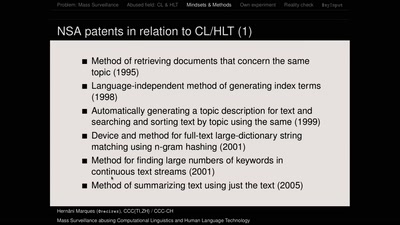
Mass Surveillance abusing Computational Linguistics and Human Language Technology
Mind-sets, state-of-the-art methods and practices according…
36 min
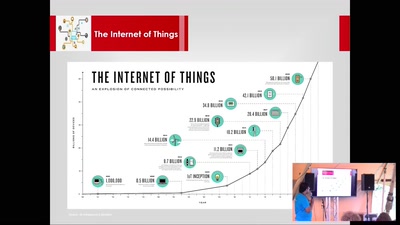
Smart Home Security with Tor
Using TOR for securing Smart Homes from prying eyes

33 min