Search for "784" returned 1851 results
56 min
Electronic Bank Robberies
Stealing Money from ATMs with Malware

60 min
Are machines feminine?
exploring the relations between design and perception of…

60 min
The Critical Making Movement
How using critical thinking in technological practice can…
60 min
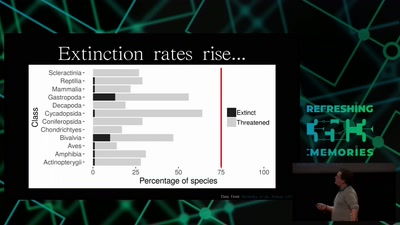
Hacking Ecology
How Data Scientists can help to avoid a sixth global…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

62 min
„Wir beteiligen uns aktiv an den Diskussionen“
Die digitale „Agenda“ der Bundesregierung aus inhaltlicher,…

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

51 min
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

43 min