Search for "tor" returned 9959 results
65 min
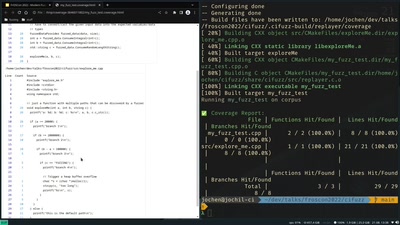
Introduction to modern fuzzing
Find and fix vulnerabilities before they reach production.

14 min
Why openSUSE is the perfect OS for handhelds
And how to bring openSUSE to your device as well!

25 min
30 seconds to Code
Streamlining development setups with Docker and Open Build…

37 min
From USA to DE.
A safe place for US hackers

78 min
An Introduction to ZFS
A Solid Foundation for Your Data

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

20 min
From Healthcare to Governments:
Building Europe’s Secure Messaging Standard

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…

52 min
From Fine to Fantastic
Beyond Static Sound Design

44 min
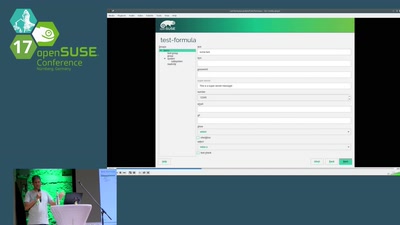
MySQL Community How To
A visual guide to MySQL community participation

47 min
From robot to robot
Restoring creativity in school pupils using robotics

51 min
From zero to Openstack
Deploying Openstack for fun and profit
28 min
Welcome to the Anthropocene?
(Did) We Accidentally a New Geological Epoch(?)
56 min
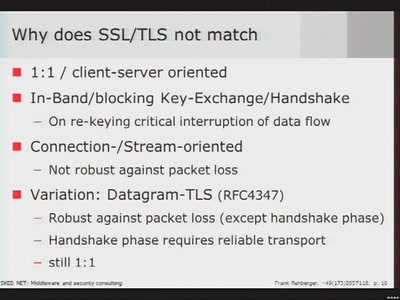
Introduction to Multicast Security
Beyond SSL/TLS
28 min