Search for "m-1-k-3" returned 9400 results

60 min
Crypto Wars Part II
The Empires Strike Back

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

62 min
Let's Encrypt
A Free Robotic Certificate Authority

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…
62 min
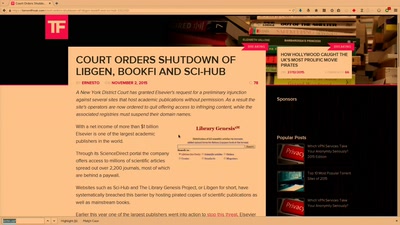
Public Library/Memory of the World
Access to knowledge for every member of society
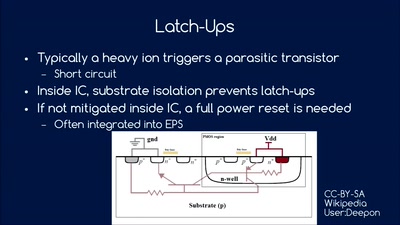
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

60 min
Hacking Reality
Mixed Reality and multi-sensory communication

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

51 min