Search for "m-1-k-3" returned 9400 results

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model

33 min
Open source experimental incubator build up
call for participation in project and product development

46 min
CounterStrike
Lawful Interception

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

42 min
All Creatures Welcome
a utopian documentary about the digital age
40 min
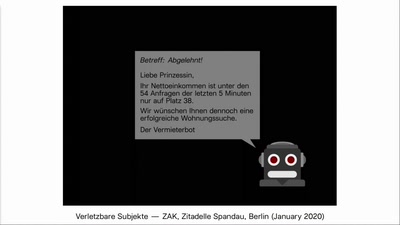
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…
60 min
Katastrophe und Kommunikation am Beispiel Nord-Ost-Syrien
Humanitäre Hilfe zwischen Propaganda, Information und…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…
38 min
Policing the Romantic Crowd
Velocipedes and Face Recognition

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

53 min
When algorithms fail in our personal lives
Social media break up coordinator

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

59 min