Search for "xian"
prev

42 min
Finishing off the Nintendo DSi

36 min
The artist behind the viral cryptid "Loab" reflects on her…

54 min
The history and costs of government exceptional access

66 min
A Rapidly Emerging Police State and Imminent Deportation to…
55 min
Preserving access to the open Internet with circumvention…

42 min
Real-world exploits and mitigations in Large Language Model…
53 min
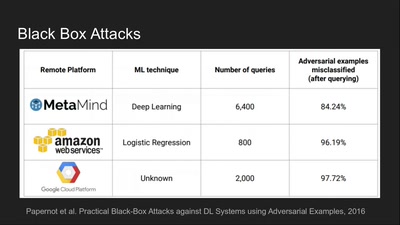
Tools for Fooling the "Black Box"

53 min
An introduction without maths
109 min
20 Jahre Fnord-Jahresrückblick!

46 min
Strong metadata protection for asynchronous messaging

58 min
weaknesses in the encryption of solid state drives (SSDs)

61 min
Internet reengineering session

46 min
--Gaining code execution using a malicious SQLite database
prev