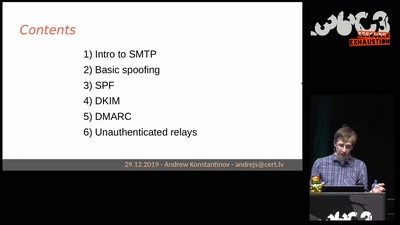
Search for "Leli"
prev
next

37 min
Don't ask what you can do for TPMs, Ask what TPMs can do…

58 min
Breaking PDF Encryption and PDF Signatures

32 min
Automatic detection of key-reuse vulnerabilities

53 min
An introduction without maths

60 min
...or why adding BTLE to a device sometimes isn't smart at…

58 min
E-ID, E-Voting, Netzsperren und andere netzpolitische…

29 min
Technical Teardown of the Pegasus malware and Trident…

44 min
Tech unexeptionalism and the monopolization of every…
61 min
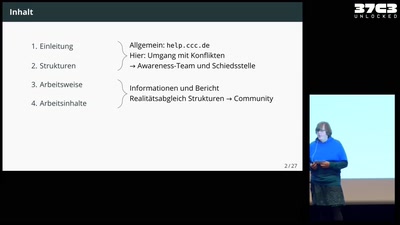
Über die Strukturen im Hintergrund: Awareness-Team und…
128 min
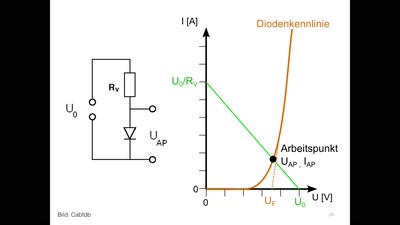
Die Wissenschaftsgala vom 32C3
43 min
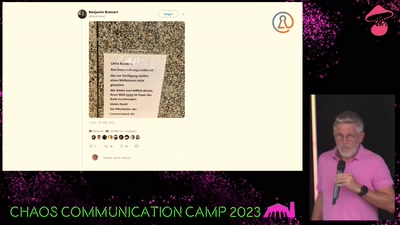
Datenschutz-Mythen aus 5 Jahren DS-GVO

41 min
How high-level scripting languages make your hardware…
71 min
Teams presenting how they helped making this awesome event

48 min
performant cross platform development using modern…
prev
next