Search for "32c3" returned 2751 results
61 min
Avoiding kernel panic: Europe’s biggest fails in digital policy-making
How the institutions fuck up, and how we fuck it up as well

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
60 min
Sin in the time of Technology
How social media companies are creating a global morality…
62 min
Public Library/Memory of the World
Access to knowledge for every member of society
60 min
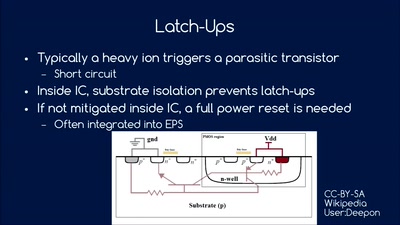
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

30 min
libusb: Maintainer fail
How I failed to run an open source project
27 min
Maritime Robotics
Hackers, I call thee to our Oceans!

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society

72 min
Console Hacking
Breaking the 3DS

69 min