Search for "26" returned 4318 results

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

43 min
Forensic Architecture
Forensic Architecture is an independent research agency…
60 min
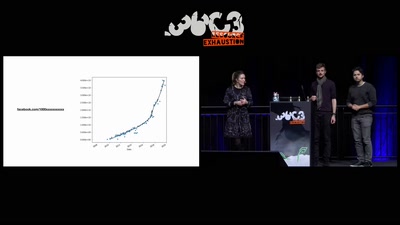
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…
46 min
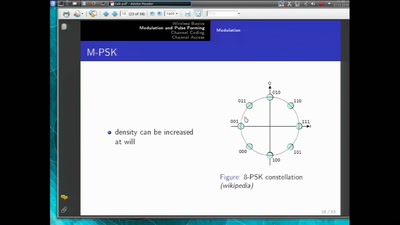
Basics of Digital Wireless Communication
introduction to software radio principles

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
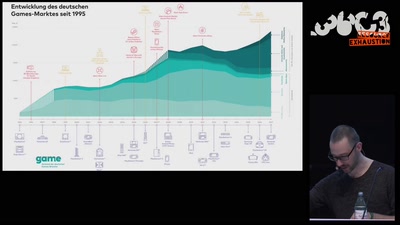
46 min
Let’s play Infokrieg
Wie die radikale Rechte (ihre) Politik gamifiziert

33 min
institutions for Resolution Disputes
Rosa Menkman investigates video compression, feedback, and…

66 min
The Snowden Refugees under Surveillance in Hong Kong
A Rapidly Emerging Police State and Imminent Deportation to…
39 min
The Eye on the Nile
Egypt's Civil Society Under Attack

63 min
goto fail;
exploring two decades of transport layer insecurity

29 min
2 Takte später
30C3S SCE mbH: GEMA-Konkurrenz für Fortgeschrittene

30 min
Syrian Archive
Preserving documentation of human rights violations

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…

34 min
Ling - High level system programming
modular and precise resource management

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

32 min
The Moon and European Space Exploration
Refocusing on the moon as a platform for future deep space…

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

60 min