Search for "26" returned 4166 results

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

31 min
TrustZone is not enough
Hijacking debug components for embedded security
31 min
Access To Bodies
Ein Leitfaden für post-humane Computer- und…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

60 min
Concepts for global TSCM
getting out of surveillance state mode

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

58 min
Paypals War on Terror
A Historical Re-Enactment of the PayPal14

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…
58 min
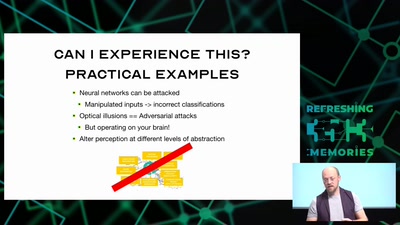
Hacking how we see
A way to fix lazy eye?

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

58 min
Überwachen und Sprache
How to do things with words

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

63 min