Search for "24" returned 4475 results
58 min
G10, BND-Gesetz und der effektive Schutz vor Grundrechten
Die strategische Fernmeldeüberwachung des BND vor dem…

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

30 min
apertus° AXIOM
The first Open Source Cinema Camera
31 min
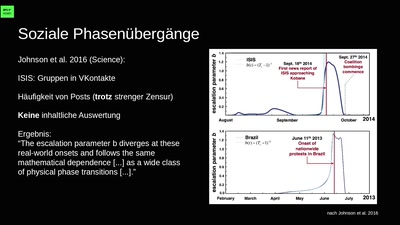
Berechnete Welt
Unsere Daten, die Zukunft und die zerstörte Demokratie

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

31 min
BGP and the Rule of Custom
How the internet self-governs without international law

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine

54 min
Do You Think That's Funny?
Art Practice under the Regime of Anti-Terror Legislation

61 min
Beeinflussung durch Künstliche Intelligenz
Über die Banalität der Beeinflussung und das Leben mit…

63 min
Reconstructing narratives
transparency in the service of justice

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

60 min