Search for "fake" returned 2878 results

36 min
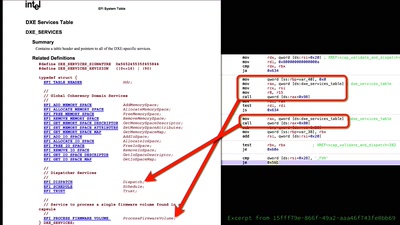
Modchips of the State
Hardware implants in the supply-chain
44 min
Spot the Surveillance
How to Identify Police Surveillance at Protests and Large…

40 min
A year of surveillance in France: a short satirical tale by La Quadrature du Net
From the so-called Country of human rights to a…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
58 min
Firebird Open Source Database Quick Start
Why Firebird is a powerful alternative database system
41 min
A WebPage in Three Acts
live coding performance
47 min
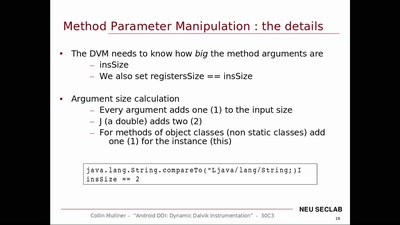
Android DDI
Dynamic Dalvik Instrumentation of Android Applications and…

60 min
net neutrality: days of future past?
Taking stock after two years of net neutrality in the…

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

62 min
Let's Encrypt
A Free Robotic Certificate Authority

33 min
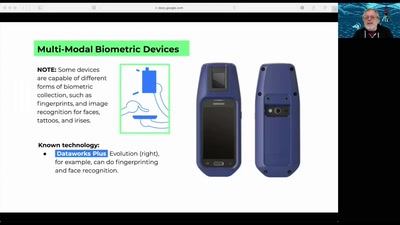
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…

61 min
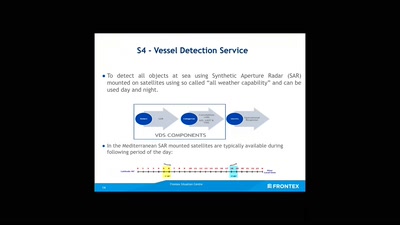
About Gamma-Ray Bursts And Boats
What We (Don't) Know About the Most Energetic Events in the…
40 min
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

30 min
Syrian Archive
Preserving documentation of human rights violations

47 min
Hardening hardware and choosing a #goodBIOS
Clean boot every boot - rejecting persistence of malicious…

32 min