Search for "38c3" returned 2550 results

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

61 min
Net Neutrality in Europe
alea iacta est
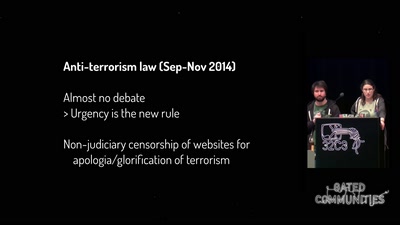
27 min
One year of securitarian drift in France
From the Bill on Intelligence to the State of Emergency

61 min
Jugend hackt 2015
Projektvorstellungen der JunghackerInnen
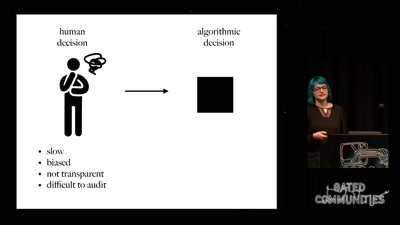
60 min
Prediction and Control
Watching Algorithms

51 min
How to contribute to make open hardware happen
Mooltipass, Openpandora/Pyra and Novena/Senoko: how I…

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP
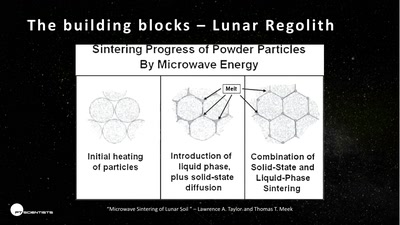
55 min
3D printing on the moon
The future of space exploration

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

60 min
Crypto Wars Part II
The Empires Strike Back

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom
56 min