Search for "m-1-k-3" returned 9403 results

43 min
Nintendo DS
Introduction and hacking

60 min
The worst part of censorship is XXXXX
Investigating large-scale Internet content filtering
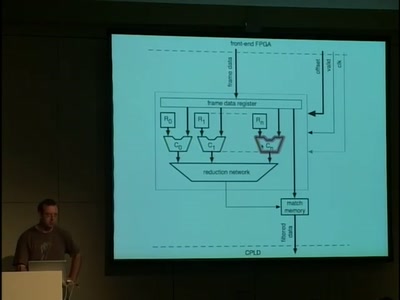
52 min
A 10GE monitoring system
Hacking a 10 Gigabit Intrusion detection and prevention…

68 min
Software Protection and the TPM
The Mac OS X Story

55 min
Black Ops 2006 Viz Edition
Pixel Fuzzing and the Bioinformatic Bindiff
56 min
Hackerspaces
How we built ours - How you can build yours

45 min
Homegrown Interactive Tables
Any Technology Sufficiently Advanced is Indistinguishable…

62 min
The Story of The Hacker Foundation
Challenges of Organizing a Foundation for Hackers in the USA

62 min
Vehicular Communication and VANETs
The future and security of communicating vehicles

56 min
Dying Giraffe Recordings: A non-evil recordlabel
Using the power of creative commons to create an…

63 min
Biometrics in Science Fiction
2nd Iteration

62 min
Detecting temperature through clock skew
Hot or Not: Defeating anonymity by monitoring clock skew to…

95 min
Analysis of a strong Random Number Generator
by anatomizing Linux' CPRNG

49 min
Ethernet mit Mikrocontrollern
Wie funktioniert TCP mit 2kb RAM?

45 min
Secure Network Server Programming on Unix
Techniques and best practices to securely code your network…

87 min
Tor and China
Design of a blocking-resistant anonymity system

47 min
How to implement bignum arithmetic
A short look at my pet project implementation

78 min
Stealth malware - can good guys win?
Challenges in detecting system compromises and why we’re so…

54 min
To live outside the law you gotta be honest
Ist nicht jedes Passwort eine Manifestation des Mißtrauens?
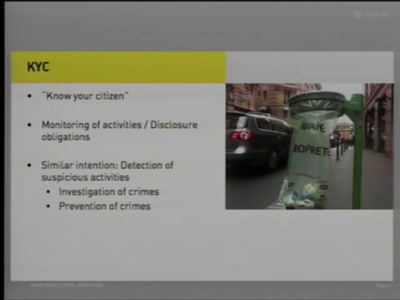
57 min
Know Your Citizens
State Authorities' Access to Sensitive Information

76 min



