Search for "m-1-k-3" returned 9403 results
44 min
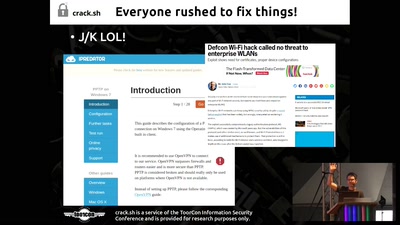
Legacy Crypto Never Dies
Cracking DES nearly 20 years after the EFF DES Cracker
60 min
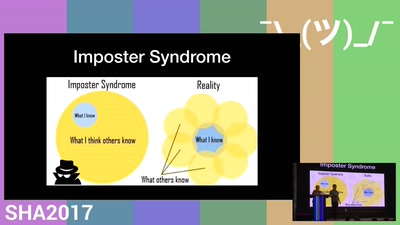
Nerd-Wrangling 101
Managing Neurodiversity with Cognitive Empathy
53 min
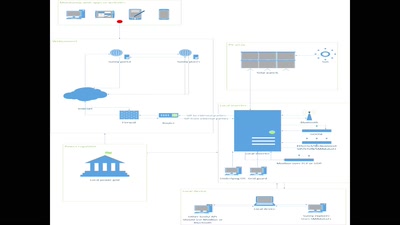
How an intern hacked the powergrid
The Horus Scenario
45 min
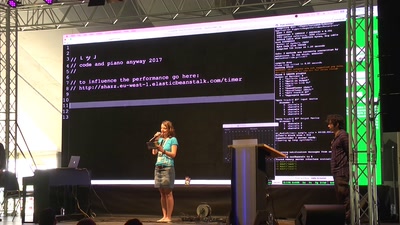
Off<>zz Code and Piano Concert
“Code Our Glance” and beta “CodeKlavier”

53 min
Smart, safe & happy
ensuring civil rights in the digital era

34 min
Digital personal locker
New paradigm in handling personal (health) data

57 min
Building Businesses that we can Buy Into and Believe In
What it means to profit from privacy-friendly, open-source…

55 min
Because "use urandom" isn't everything: a deep dive into CSPRNGs in Operating Systems &…
Implementation, hazards and updates on use of RNGs in…
48 min
Cut by the free and open edge
FLOSS, NGOs, Activists, Journalists, and the Pareto…

27 min
The law and leaky abstractions
In what ways can laws influence the security of society.

52 min
Human Rights and Internet Infrastructure
standard or substandard?

61 min
Human body as an electric IO system
Hacking your brain, and other body parts. Debunking myths…

50 min