Search for "Twi"
prev
next

56 min
How soft and hardware can play a key role in saving lives…

57 min
Hardware attacks on the latest generation of ARM Cortex-M…

64 min
The Role of Stylometry in Privacy

58 min
weaknesses in the encryption of solid state drives (SSDs)

54 min
Unlocking God Mode on Linux

32 min
From tractors to Web standards
36 min
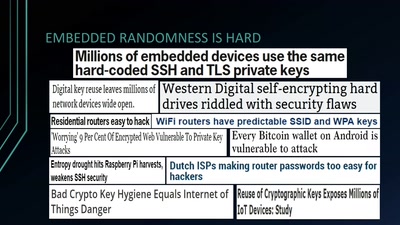
Analyzing Embedded OS Random Number Generators
42 min
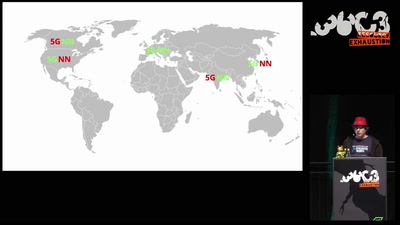
Status of the Net Neutrality Reform in Europe

50 min
Overview of how the state censored and how it got…

40 min
Call the frontdoor to install your backdoors

63 min
Moving Beyond Single Points of Failure for Software…
53 min
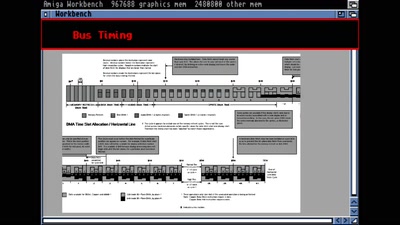
Amiga Hardware Design And Programming
56 min
PART II: disrupting disruption

31 min
Sound art performance exploring the concept of translation…

60 min
How not to do DOCSIS networks
prev
next




