Search for "hacker eg" returned 664 results
29 min
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

63 min
Synthetic Sentience
Can Artificial Intelligence become conscious?

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology

64 min
Magic Lantern
Free Software on Your Camera

44 min
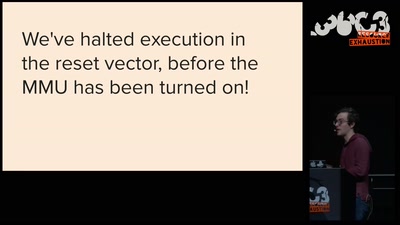
ASLR on the line
Practical cache attacks on the MMU

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…

30 min
The ArduGuitar
An Arduino Powered Electric Guitar
42 min
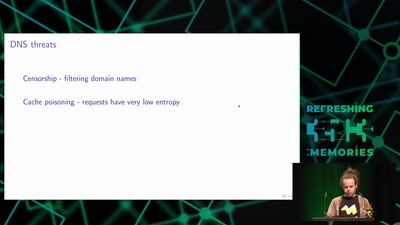
Domain Name System
Hierarchical decentralized naming system used since 30 years

46 min
CounterStrike
Lawful Interception

32 min
History and implications of DRM
From tractors to Web standards
53 min
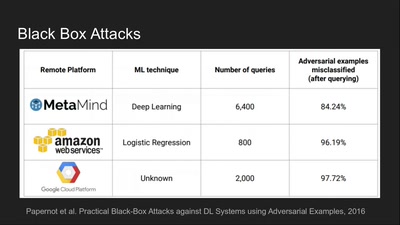
Deep Learning Blindspots
Tools for Fooling the "Black Box"

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
50 min
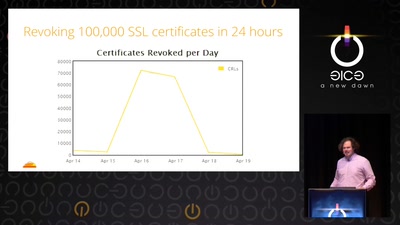
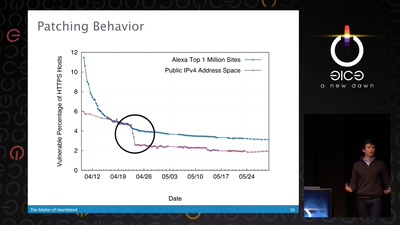
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets

32 min