Search for "Udo Vetter" returned 1111 results
59 min
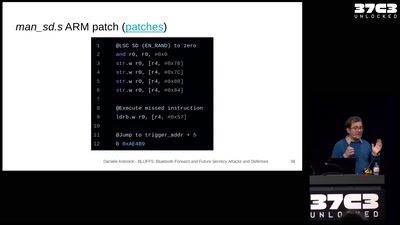
BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
Breaking and fixing the Bluetooth standard. One More Time.
32 min
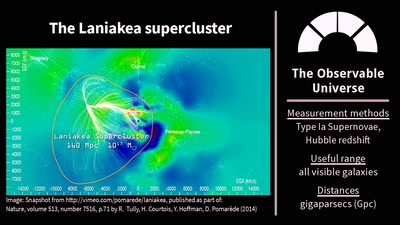
The Universe Is, Like, Seriously Huge
Stuff in Space Is Far Away – but How Do We Know?

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
When hardware must „just work“
An inside look at x86 CPU design

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

33 min
Turing Complete User
What can be done to protect the term, the notion and the…
60 min
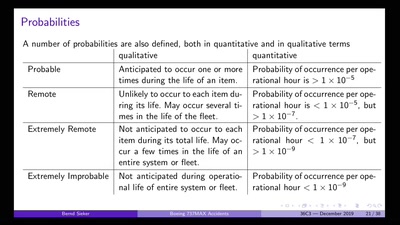
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

63 min
goto fail;
exploring two decades of transport layer insecurity

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

32 min
The Case for Scale in Cyber Security
Security Track Keynote

54 min
Do You Think That's Funny?
Art Practice under the Regime of Anti-Terror Legislation

41 min
Corona-Warn-App
Behind the scenes: Invisible, yet important

60 min