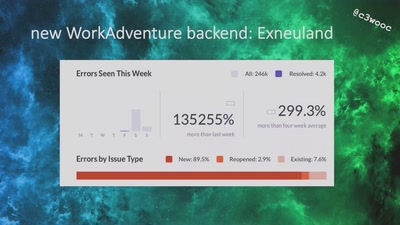
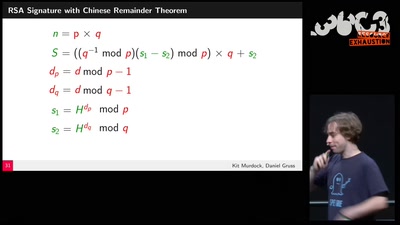
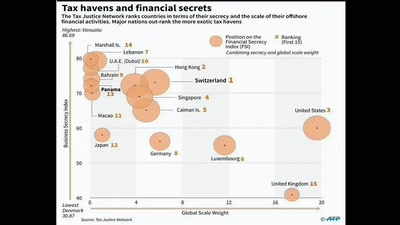
Search for ".guf" returned 4716 results

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

26 min
Technomonopolies
How technology is used to subvert and circumvent…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
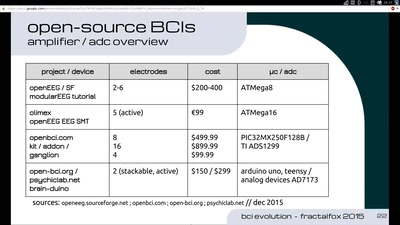
35 min
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…

30 min
Syrian Archive
Preserving documentation of human rights violations

33 min
Turing Complete User
What can be done to protect the term, the notion and the…
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

44 min
ASLR on the line
Practical cache attacks on the MMU
59 min
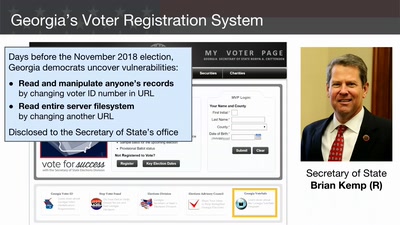
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

49 min