Search for "26" returned 4318 results

32 min
Why Do We Anthropomorphize Computers?...
...and dehumanize ourselves in the process?

43 min
Forensic Architecture
Forensic Architecture is an independent research agency…

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks
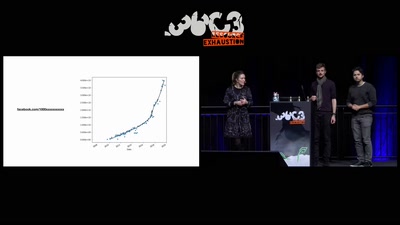
60 min
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…
46 min
Basics of Digital Wireless Communication
introduction to software radio principles

43 min
Hirne Hacken
Menschliche Faktoren der IT-Sicherheit

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
46 min
Let’s play Infokrieg
Wie die radikale Rechte (ihre) Politik gamifiziert

33 min
institutions for Resolution Disputes
Rosa Menkman investigates video compression, feedback, and…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

66 min
The Snowden Refugees under Surveillance in Hong Kong
A Rapidly Emerging Police State and Imminent Deportation to…
39 min
The Eye on the Nile
Egypt's Civil Society Under Attack
31 min
Access To Bodies
Ein Leitfaden für post-humane Computer- und…

29 min
2 Takte später
30C3S SCE mbH: GEMA-Konkurrenz für Fortgeschrittene

30 min
Syrian Archive
Preserving documentation of human rights violations

32 min