Search for "68" returned 2986 results

24 min
The Four Wars
Terror, whistleblowers, drugs, internet

58 min
Schweiz: Netzpolitik zwischen Bodensee und Matterhorn
E-ID, E-Voting, Netzsperren und andere netzpolitische…
60 min
Compileroptimierungen für Forth im Microcontroller
Mecrisp intern

61 min
How Alice and Bob meet if they don't like onions
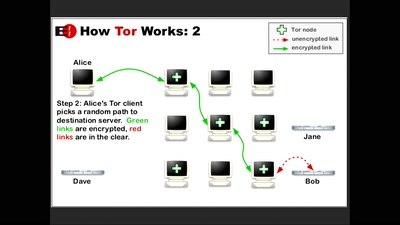
Survey of Network Anonymisation Techniques
60 min
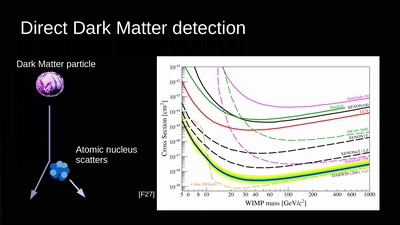
Let's reverse engineer the Universe
exploring the dark

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

58 min
Wie klimafreundlich ist Software?
Einblicke in die Forschung und Ausblick in die…

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

26 min
Humans as software extensions
Will You Be My Plugin?

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…

51 min