Search for "12" returned 5156 results

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

63 min
Through a PRISM, Darkly
Everything we know about NSA spying

61 min
Die dreckige Empirie
Kann man empirischen Studien trauen?

61 min
Dead Man Edition
Auf dem Weg zu fairer Elektronik am Beispiel der Elkos …
62 min
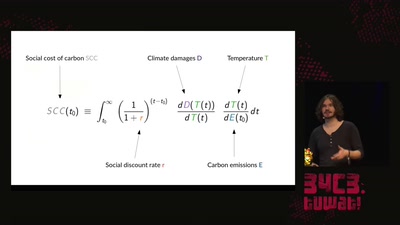
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
31 min
GIFs: Tod eines Mediums. Und sein Leben nach dem Tod.
Wie es kommt, dass technischer Fortschritt den Nutzern…

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

61 min