Popular Events
All - 2025 - 2024 - 2023 - 2022 - 2021 - 2020 - 2019 - 2018 - 2017 - 2016 - 2015 - 2014 - 2013 - 2012 - 2011 - 2010 - 2009 - 2008 - 2007 - 2006 - 2005 - 2004 - 2003 - 2002 - 2001 - 2000
59 min
Echtes Netz
Kampagne für Netzneutralität

26 min
ChokePointProject - Quis custodiet ipsos custodes?
Aggregating and Visualizing (lack of) Transparancy Data in…

21 min
Closing Event
Good Bye and have a safe trip home!

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes
47 min
Test-Driven Web Development
Treating your web application like the grown-up it is
107 min
Pentanews Game Show 2k11/3
42 new questions, new jokers, same concept, more fun than…

43 min
Strahlung im Weltall
Hell yeah, it's radiation science!

51 min
Deduplication
Wie funktioniert es? Wofür kann man es Nutzen? Wofür nicht?

45 min
Your Disaster/Crisis/Revolution just got Pwned
Telecomix and Geeks without Bounds on Security and Crisis…

61 min
Electronic money: The road to Bitcoin and a glimpse forward
How the e-money systems can be made better

39 min
Freie Software - wer wie was, wieso weshalb warum
Eine kurze Einführung

65 min
There's Gold in Them Circuit Boards
Why E-Waste Recycling Is Smart and How To Make It Smarter
51 min
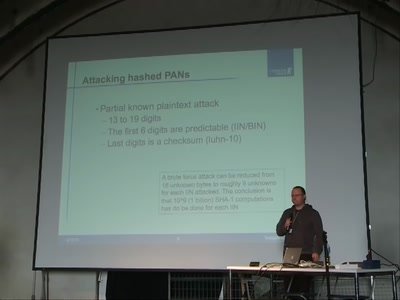
Strong encryption of credit card information
Attacks on common failures when encrypting credit card…
60 min