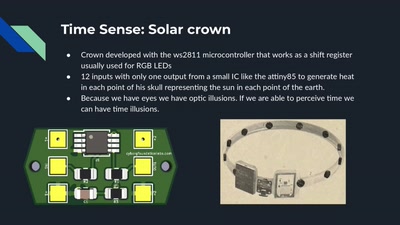
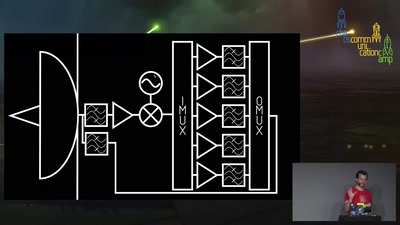
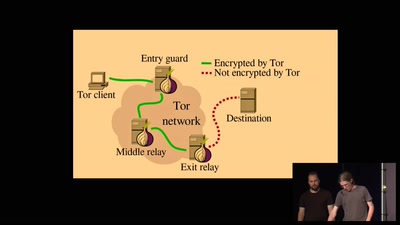
39 min
Strom in Bits und Bytes visualisiert
36 min
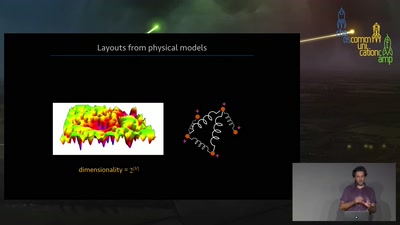
How algorithms inspired by the laws of physics can create…
44 min
Technology, Intuitions & Moral Expertise

41 min
Nym Anonymous Authentication Credentials
34 min
The why and how of game jams
38 min
A tale of four generations

31 min
Ein Blick auf die Zukunft der Freifunk-Hardware (und was…

39 min
TeXnische Aspekte und Umsetzung in der DS-Redaktion
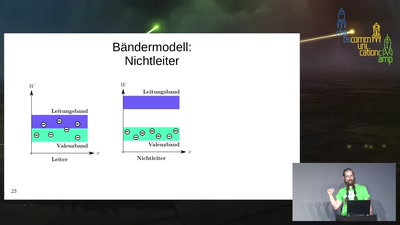
41 min
Solarzellen können nicht nur Strom erzeugen

30 min
How to educate society through the language of art

48 min
An Inquiry into the Limits of the Possible
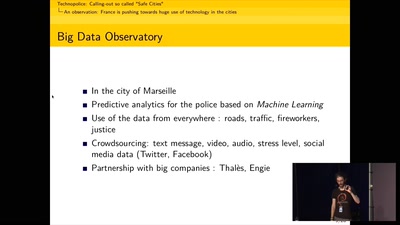
39 min
Decentralising the fight against automated surveillance in…
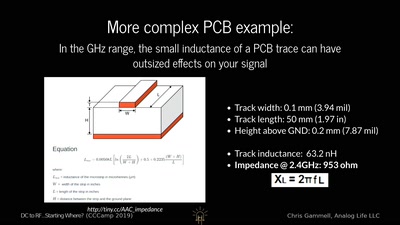
43 min
An analog engineer dives into RF circuits
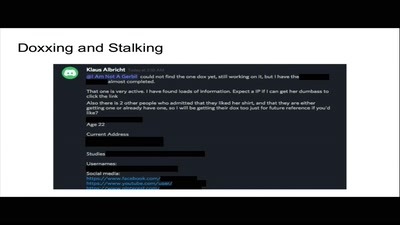
45 min
A Study of Privacy as Privilege in Our World

41 min
The Price of Energy and Reducing CO2 Emissions

50 min
Wie die Industrie mit Debatten um "ethische KI" Zeit kauft
46 min
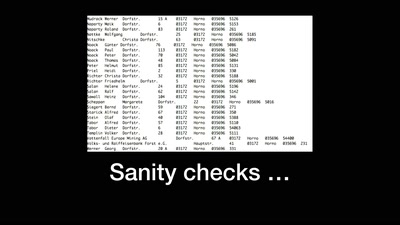
Spurensuche in elektronischen Teilnehmerverzeichnissen
47 min
How to make (nearly) everything from electricity.
42 min
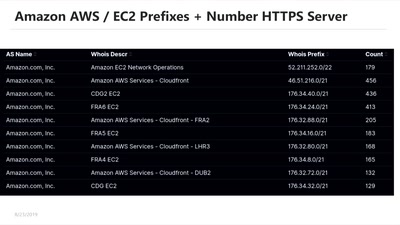
Or how to become your own ISP
51 min
Wie das Fusion Festival sich erfolgreich gegen anlasslose…
43 min
Collide, connect, cartography
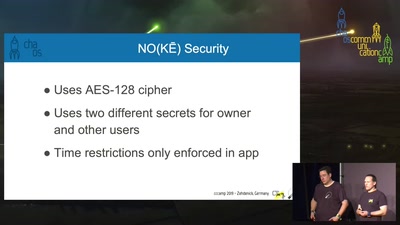
46 min
...or the 37th floor of a Hotel

41 min
"Nicht dem Phänomen Cybercrime im engeren Sinne zuzuordnen"…
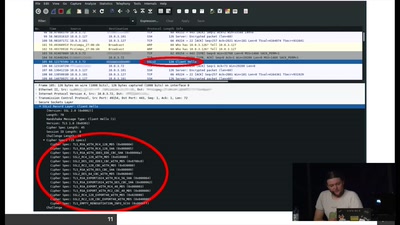
30 min
Über die (Un-)Sicherheit eines Bezahlsystems
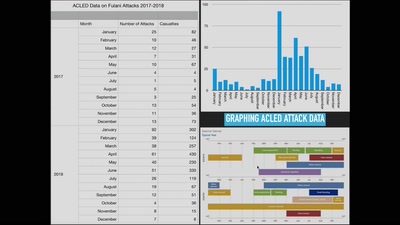
42 min
Using OSINT to monitor and predict environmental conflicts
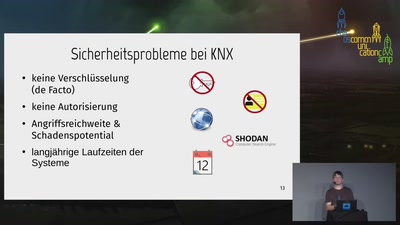
46 min
Was kann man noch retten, wenn langlebigen Strukturen…

37 min
5 Years of Disruption Network Lab

46 min
statt Digital und Dreckig
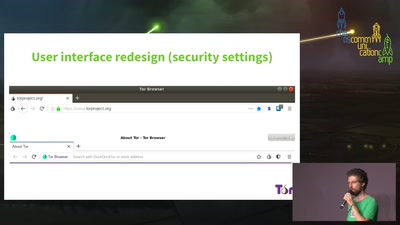
43 min
The Road to Mobile Tor and Improved Censorship Circumvention
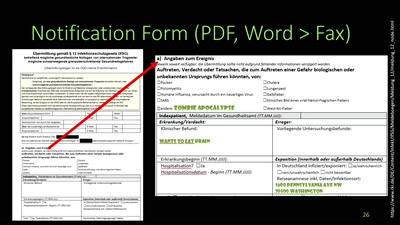
42 min
Introducing a very important piece of international law and…

40 min
Owning machines through relaying and delegation

43 min
Vom Widerstand gegen Braunkohletagebaue, die…
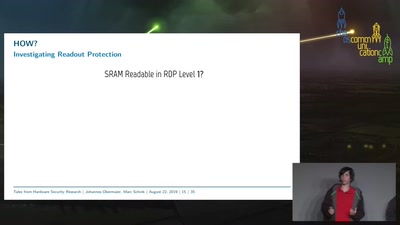
45 min
From Research over Vulnerability Discovery to Public…
44 min
The Impact of Anti-Extremism Content Regulation on Human…

49 min
secure your apps and servers through continuous integration
39 min
Cops Gegen Telekoms im ETSI

45 min
A Peek at Chinese Online Culture under the Censorship

45 min
Experiences and lessons learned from 2 years of development…

44 min
Retiring the BSD Socket API

43 min
how to make NetBSD a better software for you and me

46 min
Redesigning NoScript’s UX
34 min
Warum IMSI Catcher schlecht "Verstecken" spielen

108 min
Die große Datenschutz- und DSGVO-Show
32 min
Open source tools for flash emulation and research

86 min
die Evolution des Chaos Communication Camps
43 min
Or, making hackercamp installations for cheap
46 min
Why an SDR board like a USRP or LimeSDR is not a cellular…

33 min
Can you knot or can you not ?

45 min
How is our fight impacted by the new EU political landscape?
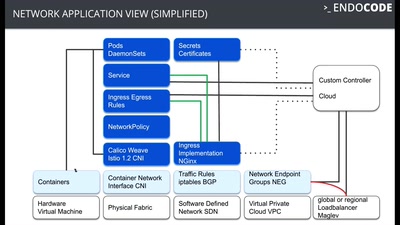
43 min
Exploiting and protecting containers with a few lines of…
43 min
Asking for better standards of official investigation and…
43 min
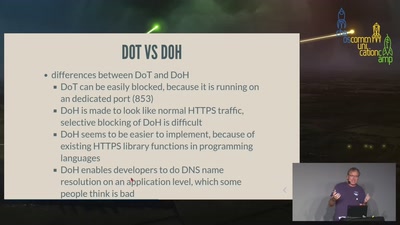
The dilemma of DNS privacy protocols
51 min
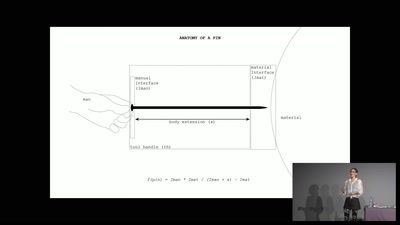
Stories from an e-textile tailor
41 min
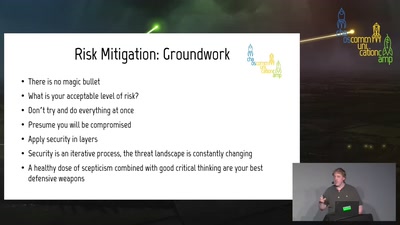
A beginner-friendly guide to network segmentation for…