48 min
Chasing GRX and SS7 vulns
46 min
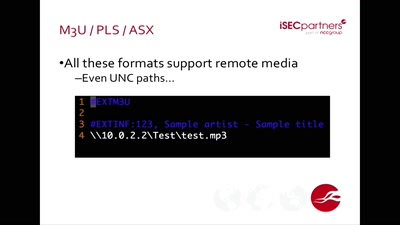
Is Your Document Telling on You?
28 min
How to retrieve secret keys without going bankrupt
56 min
Targeted threats to civil society
58 min
How did GCHQ do it to the Guardian's copy of Snowden's…
55 min
Get a verifiable path from source to binary

29 min
How to freely share research without being arrested
42 min
A Certificate Authority To Encrypt the Entire Web

30 min
Stop being tracked online
52 min
How Man-in-the-Middle filtering solutions harm the security…










