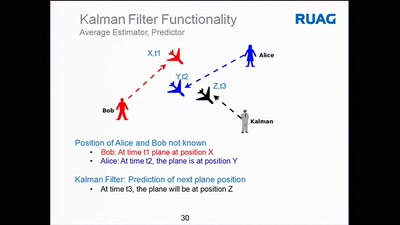
57 min
A Standard-Compliant Exploit of Layer 1
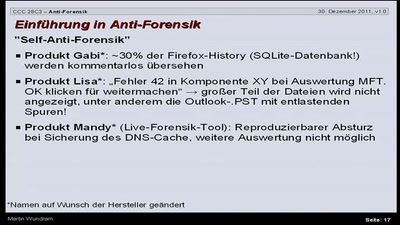
32 min
Einführung in das Thema Antiforensik am Beispiel eines…

51 min
How you end up being the Victim.

62 min
Hell Yeah, it's rocket science

62 min
Introduction into State-of-the-Art Hearing Aid Technology

53 min
Hackers need satellites. Hackers need internet over…

64 min
Die Technik der Eisenbahnsicherungsanlagen
62 min
GPRS, EDGE, UMTS, HSPA demystified

26 min
Aggregating and Visualizing (lack of) Transparancy Data in…

26 min
Insights into a publicly available registry

67 min
Welchen Wert haben Trackingdaten?

41 min
Technical defense against data retention law

59 min
Tools to Maintain Anonymity Through Writing Style & Current…

128 min
Vom braunen Briefumschlag bis zur Publikation

26 min
A new approach of identifying vulnerable web applications
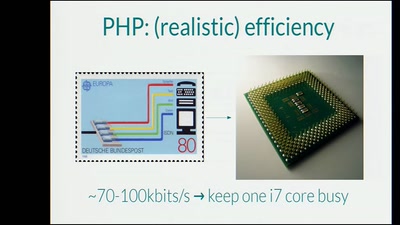
56 min
We are the 99% (CPU usage)

55 min
Bachelorarbeit Informatik Uni Kiel SS 2011
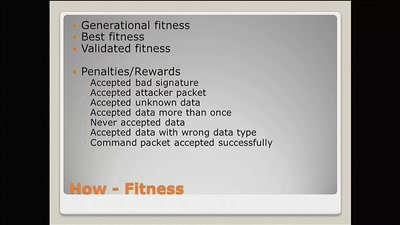
57 min
Hell Yeah, it's rocket science
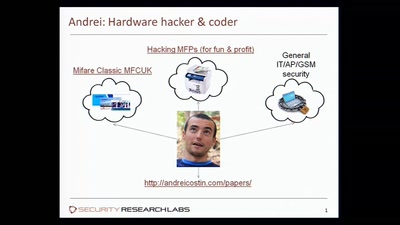
57 min
Part2 - PostScript: Um, you've been hacked
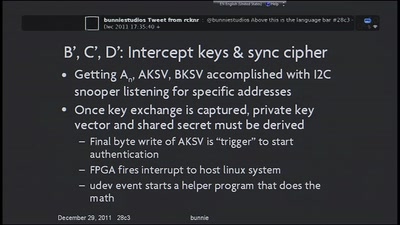
45 min
A non-copyright circumventing application of the HDCP…

55 min
Building a sniffer for the GMR satphones
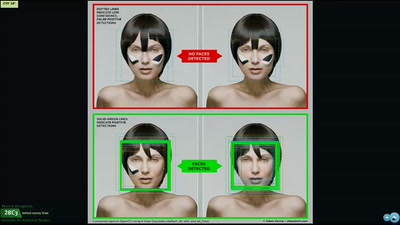
60 min
What happens when data collection goes awry in the 21st…
34 min
NOC Review about the Camp 2011 and the 28C3
28 min
Why auditing proprietary protocols matters

62 min
Automating exploitation of invalid memory writes

63 min
escape the basement and make the sun work for you

63 min
Firmware Modification Attacks and the Rise of Printer…

65 min
Transhumanism, Self-Optimization and Neurofeedback for…

56 min
Achieving a permanent stealthy compromise of user accounts…
51 min
Tiffany Rad, Teague Newman, John Strauchs

25 min
What's inside your network?
64 min
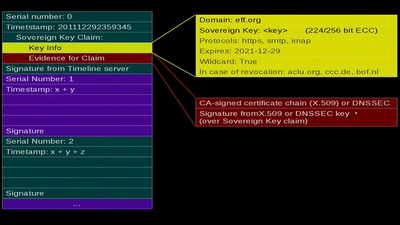
A proposal for fixing attacks on CAs and DNSSEC

47 min
Circumventing ASLR, DEP, and Other Guards
60 min
The history, the hardware and how to write programs

52 min
Why just lying your way in won't get you anywhere
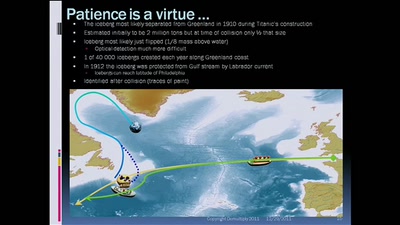
56 min
RMS Olympic, RMS Titanic, HMHS Britannic vs Discrete…
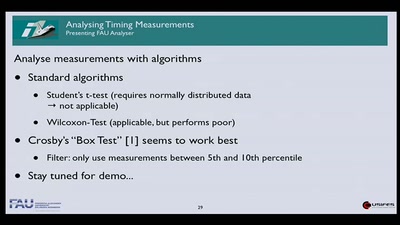
61 min
Exploiting Timing Side Channel Vulnerabilities on the Web

45 min
Telecomix and Geeks without Bounds on Security and Crisis…